- What Is Container Security?
-
Managing Permissions with Kubernetes RBAC
- Kubernetes RBAC Defined
- Why Is RBAC Important for Kubernetes Security?
- RBAC Roles and Permissions in Kubernetes
- How Kubernetes RBAC Works
- The Role of RBAC in Kubernetes Authorization
- Common RBAC Permissions Risks and Vulnerabilities
- Kubernetes RBAC Best Practices and Recommendations
- Kubernetes and RBAC FAQ
- Kubernetes: How to Implement AI-Powered Security
- What Is Container Runtime Security?
- What Is Kubernetes Security?
-
Multicloud Management with Al and Kubernetes
- Multicloud Kubernetes Defined
- How Does Kubernetes Facilitate Multicloud Management?
- Multicloud Management Using AI and Kubernetes
- Key AI and Kubernetes Capabilities
- Strategic Planning for Multicloud Management
- Steps to Manage Multiple Cloud Environments with AI and Kubernetes
- Multicloud Management Challenges
- Kubernetes Multicloud Management with AI FAQs
-
What Is Kubernetes?
- Kubernetes Explained
- Kubernetes Architecture
- Nodes: The Foundation
- Clusters
- Pods: The Basic Units of Deployment
- Kubelet
- Services: Networking in Kubernetes
- Volumes: Handling Persistent Storage
- Deployments in Kubernetes
- Kubernetes Automation and Capabilities
- Benefits of Kubernetes
- Kubernetes Vs. Docker
- Kubernetes FAQs
-
What Is Kubernetes Security Posture Management (KSPM)?
- Kubernetes Security Posture Management Explained
- What Is the Importance of KSPM?
- KSPM & the Four Cs
- Vulnerabilities Addressed with Kubernetes Security Posture Management
- How Does Kubernetes Security Posture Management Work?
- What Are the Key Components and Functions of an Effective KSPM Solution?
- KSPM Vs. CSPM
- Best Practices for KSPM
- KSPM Use Cases
- Kubernetes Security Posture Management (KSPM) FAQs
- What Is Orchestration Security?
- What Is Container Orchestration?
-
How to Secure Kubernetes Secrets and Sensitive Data
- Kubernetes Secrets Explained
- Importance of Securing Kubernetes Secrets
- How Kubernetes Secrets Work
- How Do You Store Sensitive Data in Kubernetes?
- How Do You Secure Secrets in Kubernetes?
- Challenges in Securing Kubernetes Secrets
- What Are the Best Practices to Make Kubernetes Secrets More Secure?
- What Tools Are Available to Secure Secrets in Kubernetes?
- Kubernetes Secrets FAQ
-
Kubernetes and Infrastructure as Code
- Infrastructure as Code in the Kubernetes Environment
- Understanding IaC
- IaC Security Is Key
- Kubernetes Host Infrastructure Security
- IAM Security for Kubernetes Clusters
- Container Registry and IaC Security
- Avoid Pulling “Latest” Container Images
- Avoid Privileged Containers and Escalation
- Isolate Pods at the Network Level
- Encrypt Internal Traffic
- Specifying Resource Limits
- Avoiding the Default Namespace
- Enable Audit Logging
- Securing Open-Source Kubernetes Components
- Kubernetes Security Across the DevOps Lifecycle
- Kubernetes and Infrastructure as Code FAQs
- What Is the Difference Between Dockers and Kubernetes?
- Securing Your Kubernetes Cluster: Kubernetes Best Practices and Strategies
- What Is Docker?
- What Is Container Registry Security?
- What Is a Container?
- What Is Containerization?
What Is a Host Operating System (OS)?
A host OS in containerized systems is the underlying operating system that runs on the physical or virtual machine where the containers are deployed. The host OS manages the system's hardware resources and provides a runtime environment for container engines like Docker or containerd.
Containers running on the host OS share the same kernel as the host, but they have their own isolated user space, which includes the application, its dependencies, and libraries. The host, then, allows containers to be lightweight, portable, and efficient compared to applications running on separate virtual machines.
The Host Operating System (OS) Explained
When deploying containerized applications, the host OS works in tandem with the container runtime engine, such as Docker or Kubernetes, to manage the lifecycle of containers. The container runtime engine pulls the required container images, creates container instances, and starts them within the user space of the host OS. As containers share the kernel of the host OS but run in isolated user spaces, the host OS ensures that the necessary resources, such as CPU and memory, are efficiently allocated and managed for each container.
The host OS also plays a role in maintaining security and access control for containerized applications. It enforces security policies, authentication, and authorization to protect the system from unauthorized access and potential threats. In addition, the host OS helps in monitoring and logging container activities, providing valuable insights into the performance and potential issues.
By working together with the container runtime engine, the host OS creates a seamless environment for deploying, scaling, and managing containerized applications across various computing environments. The host OS ensures that containerized applications run consistently and securely while efficiently utilizing the underlying hardware resources.
Host OS Selection
Selecting the appropriate host operating system and properly hardening it are key aspects of ensuring container security. When evaluating potential host OS options, consider factors such as the kernel version, built-in container runtime support, and pre-installed security modules. A recent Linux kernel (version 3.10 or newer) is preferable, as it enables advanced features such as cgroups v2 and user namespaces, which provide improved isolation and resource management capabilities for containers.
Container-optimized operating systems, such as Container Linux by CoreOS or RancherOS, offer a minimal installation with reduced attack surfaces, as well as built-in support for container runtimes like Docker or containerd. These operating systems often come preconfigured with security modules like SELinux or AppArmor, which enforce mandatory access control (MAC) policies on container processes.
Comparison of Popular Host OS Options
Container-optimized operating systems offer a minimal installation with reduced attack surfaces, as well as built-in support for container runtimes like Docker or containerd. Experienced practitioners should consider several factors when evaluating host OS options, including compatibility with container runtimes, orchestration tools, and other components necessary for the containerized environment.
Ubuntu
Ubuntu is a widely used Linux distribution that offers extensive support, frequent updates, and compatibility with various container runtimes and orchestration tools. With AppArmor for security hardening and a minimal server edition for reduced resource usage, Ubuntu presents a versatile option for many container environments.
CentOS
CentOS, popular in enterprise settings, is a community-supported distribution derived from Red Hat Enterprise Linux (RHEL). It features SELinux for security, compatibility with container runtimes, and long-term support, making it a reliable choice for organizations seeking stability.
CoreOS
CoreOS, now known as Container Linux, is designed for running containers. It’s lightweight and minimalistic, featuring automatic updates, support for Docker and rkt container runtimes, and built-in security features like SELinux and cgroups.
RancherOS
RancherOS is a purpose-built OS for container environments, designed to run Docker containers. It boasts a minimal footprint, rapid boot times, and simplified management through Rancher orchestration tools.
Host OS Security
The host operating system serves as the foundation on which container runtimes operate, handling hardware interactions and supplying system resources to containers. To improve Kubernetes security, it’s recommended to use a streamlined and lightweight version of an operating system, which minimizes the attack surface by including only essential components. Hardening the host OS, applying security patches, and maintaining minimal privileges are key to enhancing container security.
In Figure 1, we see an order of components that emphasizes the importance of securing the underlying infrastructure before moving to container-specific security measures. Despite the host OS’ foundational role, it’s often overlooked when securing container environments.
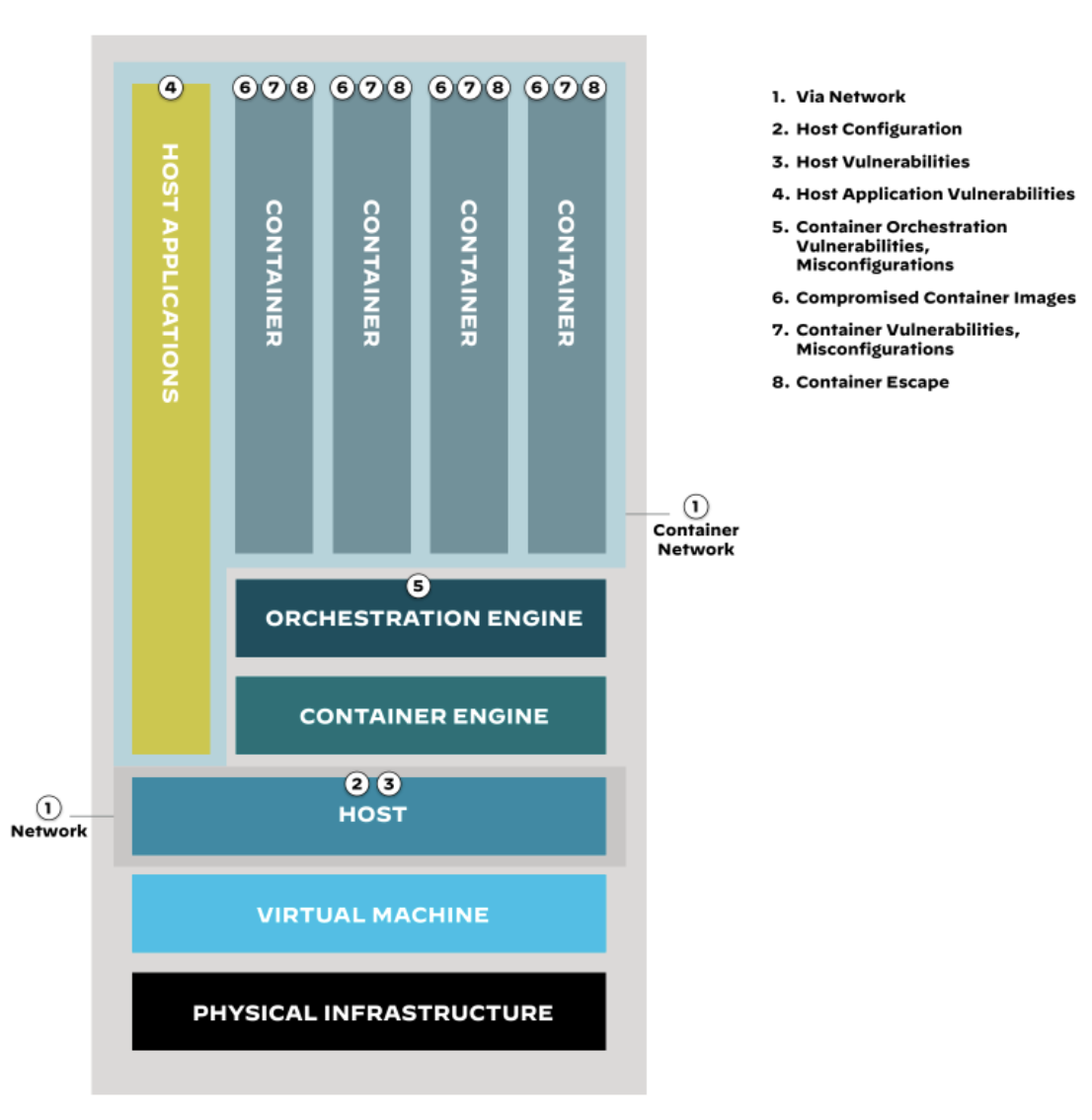
Figure 1: Anatomy of the container attack surface
Host OS security involves many aspects — scanning for vulnerabilities, hardening the system based on industry benchmarks (such as NIST, SANS, or CIS), and safeguarding against improper access control (e.g., Docker commands, SSH commands, sudo commands) or file tampering. Both Linux and Windows-based OS are commonly used and supported by most orchestration vendors, depending on the application.
When deploying on private infrastructure, ensure compliance with the minimum hardware requirements and choose a compatible OS, such as Linux or Windows, supported by your orchestration vendor.
By prioritizing host OS security, you can establish a strong foundation for your container environment, protecting your applications and maintaining overall system integrity.
Implement Industry-Standard Security Benchmarks
To ensure a consistent and secure host OS configuration, adhere to industry-standard security benchmarks. The Center for Internet Security (CIS) provides comprehensive benchmarks for various host OS options. These benchmarks offer configuration guidelines for system settings, security controls, and validation and testing procedures. Following these recommendations will help maintain a secure host OS while running container workloads.
Customizing OS Configurations for Improved Security
Hardening the host OS for container environments involves several steps. Start by disabling unnecessary services to reduce the attack surface and minimize resource usage. Close unused network ports to prevent unauthorized access, and remove unneeded applications and packages to reduce potential vulnerabilities. Restrict the use of insecure protocols and enable secure alternatives, such as using SSH over Telnet or HTTPS over HTTP. Finally, enable and configure security features like SELinux, AppArmor, or cgroups to enforce access controls and resource isolation. Regularly review system configurations and remove unused software packages to maintain a secure and up-to-date environment.
Container Escape
To understand potential host OS security threats, let’s look at container escape, a security event where malicious actors can leverage a containerized application's vulnerabilities to breach its isolation boundary from the OS and gain access to the host system's resources and other containers.
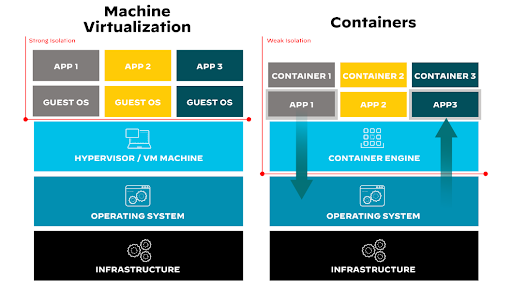
Figure 2: Architectural isolation difference between a container and a VM
In general, virtualized hardware isolation provides a stronger security boundary than namespace isolation. The risk of an attacker escaping a container (process) is much higher than escaping a VM due to the weaker isolation created by namespace and cgroup.
Linux implements namespace and cgroup by associating new property fields with each process. These fields, found in the /proc file system, inform the host OS about process visibility and the CPU/memory resources the process can use. From the host OS perspective, a container process appears just like any other process on the host.
Traditional containers, such as Docker or LXC, aren't usually considered sandboxed containers sharing the same host and kernel. Consequently, container escape vulnerabilities can arise. Exploits of container runtime code, like runC (CVE-2019-5736), exemplify such escapes via newly discovered vulnerabilities.
In addition to software vulnerability attack vectors, misconfigurations, such as deploying a container with excessive privileges or critical mount points, can lead to container escape. Container breakout has been a long-standing concern for security teams. Risks can be mitigated, though, by following best practices, such as the Center for Internet Security's (CIS) benchmarks for Docker and Kubernetes (refer to sections 4.1 and 1.7.2, respectively).
Given these exploitable vulnerabilities, it's crucial to understand the risks when deploying containers in a multitenant cluster or having containers with sensitive data co-locate with other untrusted containers.
System-Level Security Features
Implementing system-level security features protects both the host OS and the containers running on it. One key aspect is process isolation. Linux namespaces offer a powerful mechanism for isolating container processes and resources, including process IDs (PIDs), network interfaces, inter-process communication (IPC), hostnames, file system mount points, and user IDs. By leveraging namespaces, containers can run in isolated environments with minimal impact on each other and the host OS.
In addition to namespaces, Seccomp profiles, a Linux kernel feature, contribute to the overall security of the container environment by restricting the system calls that a container can execute. Seccomp profiles provide a way to define a whitelist or blacklist of system calls, reducing the potential attack surface.
Role of SELinux, AppArmor, and cgroups in Host OS Security
SELinux (Security-Enhanced Linux), AppArmor, and cgroups play essential roles in securing the host OS for containers. SELinux enforces mandatory access controls (MAC) by restricting processes and users based on predefined security policies. AppArmor, similar to SELinux, confines applications to a limited set of resources and permissions, isolating them from the rest of the system.
Control groups (cgroups) are a Linux kernel feature that allows the limitation and prioritization of resources — such as CPU time, system memory, network bandwidth, or combinations of these resources — for a set of processes. In containerization technologies, they’re essential for efficient resource utilization and ensuring that containers run in isolation and don't monopolize system resources, which helps maintain overall system stability and security (by preventing resource exhaustion attacks).
By setting limits on CPU, memory, I/O, and other resources, administrators can ensure that container workloads don’t consume excessive resources, potentially impacting other containers or the host OS.
Enabling and Configuring Mandatory Access Controls (MAC)
Mandatory access controls (MAC) are essential for securing container environments, as they enforce strict security policies that prevent unauthorized access and resource usage. To enable and configure MAC, follow these steps:
- Choose a MAC system like SELinux or AppArmor, based on the host OS and compatibility with container runtimes and orchestration tools.
- Configure the MAC system according to the security requirements and policies of your organization, including defining security labels, profiles, and permissions.
- Test the MAC configuration to ensure it effectively restricts access and resource usage according to the defined policies.
Implementing Strong User Authentication and Access Controls
Strong user authentication and access controls help secure the host OS. Implement SSH key-based authentication to replace less secure password-based authentication, reducing the risk of unauthorized access. Additionally, consider enabling two-factor authentication (2FA) to add an extra layer of security.
To manage user access, establish a role-based access control (RBAC) system that defines roles and permissions based on the principle of least privilege. Assign users to roles that grant them the minimum level of access necessary to perform their tasks.
Patch Management and Vulnerability Management
Maintaining up-to-date software is a fundamental aspect of container security. Effective patch management and vulnerability management processes are necessary to ensure that the host OS, container images, and application dependencies remain secure.
Automating patch management and security compliance checks
Automation is key to maintaining a secure and compliant host OS. Implement automated patch management tools that monitor, download, and install updates according to predefined schedules and policies. Additionally, use automated security compliance checks to validate the host OS's adherence to security benchmarks and organizational policies.
To achieve effective patch management, automation is key. Implement automated patch management tools such as Ansible, Puppet, or Chef that monitor, download, and install updates according to predefined schedules and policies. Regularly updating the host OS, container images, and application dependencies helps to address security vulnerabilities and maintain a secure environment.
Monitoring and Managing Software Vulnerabilities in the Host OS
Vulnerability management involves several steps, including scanning, prioritizing, remediating, and validating fixes. Integrating vulnerability scanning tools, such as OpenSCAP or Trivy, into the CI/CD pipeline allows for early detection of vulnerabilities in container images and application dependencies. By establishing a vulnerability management process, organizations can ensure that security issues are addressed in a timely and effective manner, minimizing the risk of exploitation.
File System and Storage Security
Securing the file system and storage used by containers is critical for preventing unauthorized data access and tampering. To achieve this, mount the host file system with options such as "nodev," "nosuid," and "noexec" to prevent device access, setuid execution, and executable file execution, respectively. Implement granular access controls on the host file system and container volumes using Linux Security Modules (LSMs) and Access Control Lists (ACLs) and assign permissions according to the least privileged principle. This approach minimizes the risk of unauthorized access or tampering.
For container storage, it’s crucial to protect data at rest and in transit. Implement encrypted file systems, such as dm-crypt or eCryptfs, to secure data at rest. Additionally, use encrypted communication channels like Transport Layer Security (TLS) to protect data in transit from unauthorized access or interception.
When using external storage solutions, such as cloud-based storage services, ensure that proper security measures are in place, including encryption and access controls. Regularly review and update security configurations for external storage to maintain a secure environment.
Monitoring and Auditing File Access and Changes Within the Host OS
Continuous monitoring and auditing of file access and changes within the host OS help detect potential security incidents and maintain compliance. Employ file integrity monitoring (FIM) tools to track modifications to critical files and directories. Configure alerts to notify security teams of unusual activity. Implement audit logging to record file access events and integrate them with security information and event management (SIEM) solutions for analysis and correlation with other security events.
Host-Level Firewall Configuration and Security
Configuring and securing the host-level firewall is essential for protecting both the host OS and the containers running on it from network-based attacks. Implementing a default deny-all policy ensures that only necessary traffic is allowed, reducing the risk of unauthorized access. To achieve this, set the default INPUT, FORWARD, and OUTPUT chains to DROP in iptables or nftables, and create allow rules for specific ports, protocols, and IP addresses as needed.
Administrators can ensure that containers operate in segregated network environments by creating network namespaces and assigning containers to separate namespaces based on their purpose and trust levels. This will restrict container access to the host network, further enhancing security.
Logging, Monitoring, and Auditing
To maintain the security of the host OS and containers, implement centralized logging and monitoring. Collect logs from the host OS, container runtime, orchestration tools, and applications to facilitate incident detection and response and identify potential security issues.
Configure syslog or journald on the host OS to collect and store logs from various sources. Use log aggregation and analysis tools, such as Elasticsearch, Fluentd, Kibana, or Cortex Cloud to consolidate and analyze logs from multiple sources. Integrate log analysis with SIEM solutions, threat intelligence feeds, and incident response processes to enhance the detection and remediation of security incidents.
Container Performance Monitoring
Monitoring container performance metrics, such as CPU usage, memory consumption, and network activity, helps identify abnormal behavior or signs of compromise. Use tools like Prometheus, Grafana, or cAdvisor to monitor container performance metrics and configure alerts for anomalous behavior.
Auditing and Compliance
Auditing is essential for ensuring ongoing compliance with security best practices and regulatory requirements. Regularly audit the host OS, container configurations, and application dependencies to identify potential security issues or areas for improvement. Use tools such as Docker Bench, Kubernetes CIS Benchmark, or Clair to audit and validate container configurations.
Tracking Container-Related Activities
Configure audit rules using the Linux audit system or other auditing tools to track container-related activities on the host OS, such as container creation, deletion, and network activity. Regularly review audit logs to identify suspicious behavior and potential security incidents. By implementing effective logging, monitoring, and auditing processes, organizations can maintain a secure container environment and respond quickly to security incidents.
Host OS Security FAQs
A container-optimized OS (COS) is a minimal and lightweight operating system specifically designed to run containerized applications. Compared to a regular Host OS, a COS has a smaller footprint and reduced attack surface, making it more secure and resource-efficient. It often comes preconfigured with container runtime support, such as Docker or containerd, and built-in security features like SELinux or AppArmor.
By focusing on container workloads, a COS simplifies management, accelerates deployment, and ensures a consistent runtime environment, providing an ideal foundation for running containers in cloud-native and distributed systems.
Kernel hardening involves implementing security measures to protect the kernel, the core of an operating system, from vulnerabilities and attacks. Techniques include minimizing the attack surface by disabling unnecessary functions and drivers, applying least privilege principles, and using security-focused compiler options to prevent buffer overflows. Regularly updating the kernel to patch known vulnerabilities is crucial.
Kernel hardening also encompasses the use of security modules like SELinux or AppArmor, which enforce access controls beyond the traditional discretionary access control models.
Access control in cloud security refers to the process of granting or denying specific requests to access and use resources. It involves authentication, authorization, and audit. Authentication verifies a user's identity, while authorization determines their access rights to resources based on policies.
Access control models like role-based access control (RBAC) and mandatory access control (MAC) are commonly used. Effective access control ensures that users and systems have the minimum necessary privileges, reducing the risk of unauthorized access and data breaches.
AppArmor is a Linux kernel security module that provides a framework for restricting programs' capabilities with per-program profiles. Unlike SELinux, which is policy-based, AppArmor uses path-based mandatory access controls. It allows system administrators to confine program capabilities by defining a set of rules that specify the files and capabilities a program may access.
AppArmor is designed to be easier to configure than SELinux, making it more accessible for administrators to implement effective security controls.
File system security in cloud environments involves implementing measures to protect data stored on file systems from unauthorized access and manipulation. It encompasses setting proper file permissions and ownership, using encryption for data at rest, and ensuring secure backups.
Advanced file system security techniques include implementing access control lists (ACLs) for fine-grained control and integrating file system audits to track changes and detect potential breaches. In cloud storage, file system security also involves configuring shared storage and network file systems, often using identity and access management (IAM) policies to control access based on user roles and responsibilities.
Network segmentation in cloud security refers to dividing a network into smaller, distinct segments or subnets. Each segment can have its own security policies and controls, limiting the spread of breaches within a network. Segmentation helps control access to sensitive data and systems, reducing the attack surface and improving overall network performance.
In cloud environments, network segmentation often involves virtual networks, subnets, and microsegmentation techniques — all of which provide granular control over traffic between individual workloads to enhance security in multitenant cloud architectures.
Namespace isolation is a method for providing lightweight virtualization. By isolating system resources such as process IDs, network interfaces, and file system mounts, namespaces ensure that processes in one namespace remain unaware of and unaffected by activities in other namespaces.
Isolation is fundamental in containerization technologies like Docker and Kubernetes, as it allows multiple containers to run on a single host without interference. Namespace isolation enhances security by limiting the scope of potential attacks; if one container is compromised, the isolation can prevent the attacker from affecting other containers or the host system.