- What Is a Cloud Workload Protection Platform (CWPP)?
- What Is a Workload?
- Agentless vs Agent-Based Security
- What is the Difference Between Web Application Firewall (WAF) and Next-Generation Firewall (NGFW)?
-
What Is Web Application and API Protection?
-
What Is an API Gateway?
- API Gateway Explained
- API Gateways for Microservices Architectures
- What Is the API Gateway Pattern?
- Challenges of API Gateways Potential Response Time Increases
- Use Cases and API Gateway Benefits
- Service Mesh Vs. API Gateway
- API Gateway Vs. Load Balancer
- API Gateways Security and WAFs
- API Gateway Solutions
- Industry Practices and Standards
- API Gateway FAQs
What Is Layer 7?
Layer 7 is the application layer and highest level of the Open Systems Interconnection (OSI) model, a conceptual framework that standardizes the functions of a communication system into seven distinct categories. Layer 7 interfaces with and provides services to application software running on a host device, facilitating end-user and application interaction. Services such as email, file transfer and web browsing all operate at this layer.
Layer 7 Explained
In the realm of network communication, Layer 7, also known as the application layer of the OSI model, holds a pivotal role in network communication. Layer 7 provides the interface between the applications we use and the underlying network over which our data must travel. Enabling interaction between the application and network services, Layer 7 presents an array of services directly to application software running on a host device.
Think of Layer 7 as the control center of the network. Just like the brain controls the human body, Layer 7 is responsible for managing and coordinating communication between different applications.
Understanding the OSI Model
The Open Systems Interconnection model is a conceptual framework used to describe how data is transmitted over a network. Developed by the International Organization for Standardization (ISO) in 1984, it is now widely accepted as a standard model for network communications.
The OSI model provides a systematic representation of network communication processes, with the individual layers responsible for specific services that contribute to the overall function of network communication. Each layer communicates with its adjacent layers. Data passes down through the layers on the sender's side, across the network, and back up through the layers on the receiver's end.
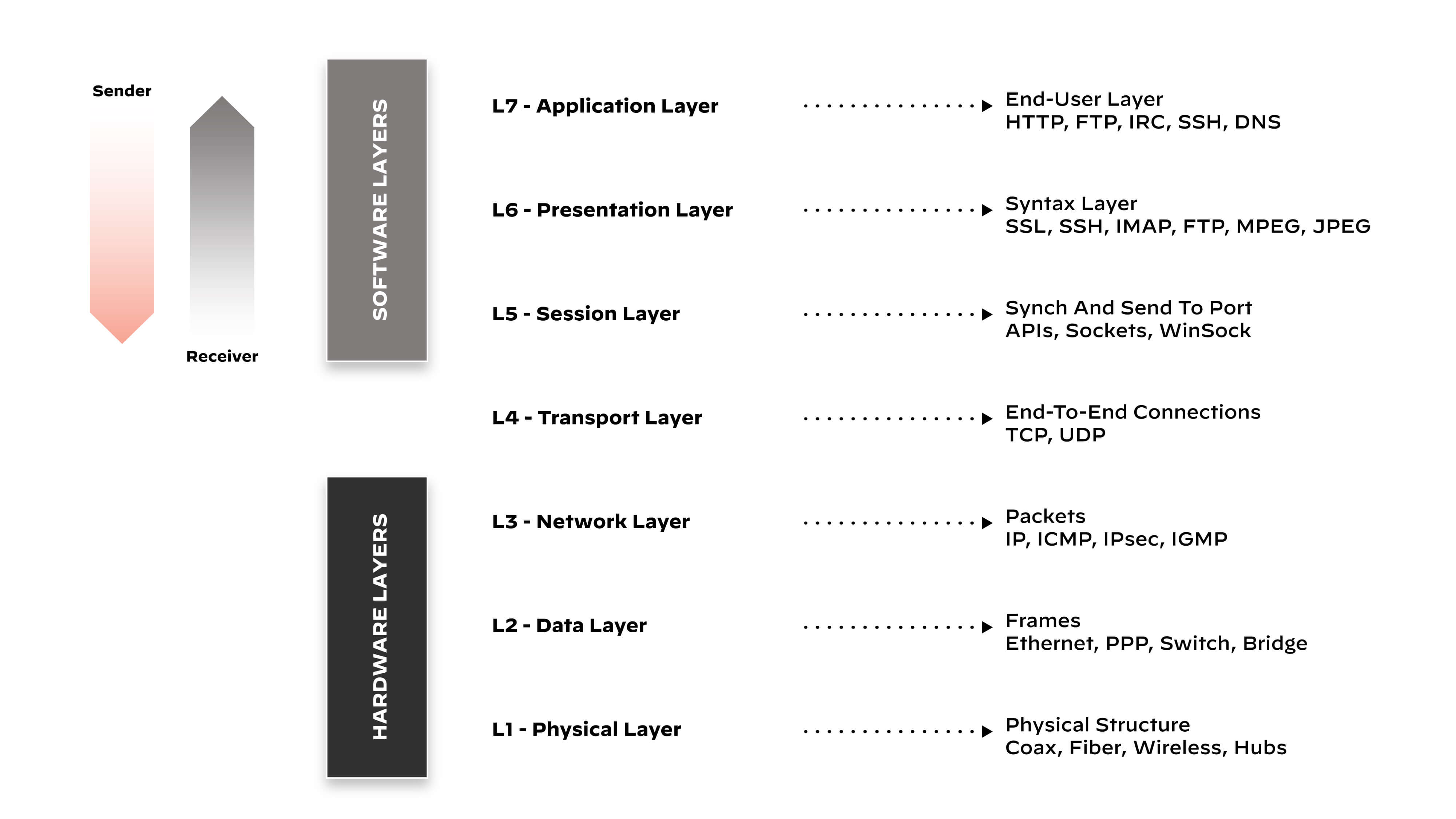
Meet the Layers of the OSI Model
Layer 1 - The Physical Layer: As the foundational layer of the OSI model, the physical layer is responsible for transmitting raw bitstream data over physical mediums like copper wire, optical fiber or radio waves. It governs aspects like bit rate, signal strength, physical connectors, cable types and network topology. Layer 1 ensures the integrity of binary transmissions across the network.
Layer 2 - The Data Link Layer: This layer structures raw bits from the physical layer into data frames and manages node-to-node communication through physical addresses (MAC addresses). Layer 2 offers error detection and correction, ensuring reliable data transmission. It also manages access to the physical medium via Carrier Sense Multiple Access with Collision Detection (CSMA/CD) and other techniques.
Layer 3 - The Network Layer: The network layer provides the means for transferring variable length data sequences (packets) from one node to another within different networks. It handles routing of packets based on logical addressing and manages network congestion and packet sequencing.
Layer 4 - The Transport Layer: Layer 4 deals with host-to-host communication between the source and destination systems. It provides mechanisms for the reliable or unreliable transmission of data via protocols like TCP and UDP and manages flow control, error checking and segmentation of data packets.
Layer 5 - The Session Layer: The session layer establishes, manages and terminates connections (sessions) between applications on each end of a communication.
Layer 6 - The Presentation Layer: The presentation layer translates application format data into a common format and vice versa, providing services such as encryption, decryption and data compression. Layer 6 ensures that data sent from the application layer of one system can be read by the application layer of another system.
Layer 7 - The Application Layer: The topmost layer of the OSI model, the application layer, serves as the interface for communication between users or processes and the network. It provides application-specific services such as HTTP requests, file transfer and email.
How Does Data Flow Through the OSI Model?
Data flows through the OSI model in a process known as encapsulation and de-encapsulation, which happens when data is sent from a source device to a destination device.
Encapsulation Process (Data Flow Downwards)
The encapsulation process starts at the application layer (Layer 7) on the source device. User data is converted into a format suitable for transmission and passed down to the presentation layer (Layer 6) for translation, compression or encryption. At the session layer (Layer 5), a session is established and maintained for the duration of the data transfer.
The transport layer (Layer 4) receives this data, divides it into manageable segments, and adds a TCP or UDP header, which includes port numbers. The network layer (Layer 3) then adds an IP header containing source and destination IP addresses, converting the segment into a packet.
The data link layer (Layer 2) encapsulates this packet in a frame, adding MAC addresses in its header and a Frame Check Sequence (FCS) in its trailer. Lastly, the physical layer (Layer 1) converts these frames into binary data (bits) for transmission over the physical medium.
De-Encapsulation Process (Data Flow Upwards)
Once data reaches the destination device, it ascends the OSI layers in a reverse process. At the physical layer, the received bits are converted back into frames. The data link layer checks the FCS for errors, removes the MAC addresses and passes the packet to the network layer.
The network layer removes the IP addresses from the packet, turning it back into a segment, which is passed to the transport layer. The transport layer verifies the correct sequencing of data, acknowledges packet receipt and removes the TCP or UDP header.
Now in its original form, the data is passed through the session and presentation layers, where the session is closed, and any translations or encryptions performed earlier are reversed. Finally, at the application layer, the original user data is delivered to the receiving application in a format it can use.
The Role of Layer 7
Layer 7 facilitates communication between software applications and lower-level network services. This layer is not concerned with the underlying details of the network but focuses on providing methods for software applications to use network services. Layer 7 essentially serves as a network interpreter that translates the user's or application's data into a standard protocol that other layers of the OSI model can understand.
Various protocols, each serving specific purposes, enable the application layer to facilitate end-to-end communication between communication partners. For instance:
File Transfer Access and Management (FTAM) protocol allows users to access and manage files in a remote system.
Simple Network Management Protocol (SNMP) enables network administrators to manage, monitor and configure network devices.
Common Management Information Protocol (CMIP) defines network management information.
HTTP (Hypertext Transfer Protocol) enables communication between clients and servers on the web.
Layer 7 Load Balancing
Load balancers distribute network traffic across multiple servers to optimize resource use, minimize response times and avoid overloading any single server.
At Layer 7, load balancing introduces an extra dimension to the distribution of network traffic. Unlike Layer 4 load balancers that base their decisions on IP address and TCP or UDP port information, Layer 7 load balancers inspect the content of the user's message to make routing decisions.
Layer 7 load balancers analyze the 'payload' of the network packet, considering elements such as HTTP headers, cookies or data within the application message to make sophisticated load balancing decisions. They can, for instance, route traffic to different servers based on the requested URL or on the type of content requested, such as images, scripts or text.
Layer 7 Security
Whether an organization opts for on-premises, cloud-based, or a hybrid approach, securing the application layer is paramount to protect sensitive data and maintain service availability. And as the layer that interfaces directly with the user and their data, Layer 7 lures bad actors determined to access user credentials and personal identifiable information. Common types of attacks at this layer include application layer attacks and Layer 7 distributed denial of service (DDoS) attacks.
Application-layer attacks attempt to exploit vulnerabilities within the application, such as poorly validated inputs or insecure configuration settings. Layer 7 DDoS attacks aim to overwhelm a server, service or network with more requests than it can handle. Unlike traditional DDoS attacks that flood networks with massive volumes of traffic, layer 7 DDoS attacks often begin slowly, mimicking normal user behavior, which makes them harder to detect.
In cloud-native environments, tools like Kubernetes provide built-in mechanisms for network security at Layer 7. These mechanisms, though, often need additional security measures, such as web application firewalls (WAFs), intrusion detection systems, and robust security policies.
WAFs, in particular, play a vital Layer 7 security role, as they operate at the application layer and can understand and make decisions based on the content of the data packet. WAFs can filter out malicious traffic based on rules defined for HTTP/HTTPS, allowing more granular control over network traffic than traditional network-layer firewalls.
OSI Model Vs. the TCP/IP Model
Like the OSI model, the Transmission Control Protocol/Internet Protocol (TCP/IP) model describes how network protocols interact and work together to provide network services. The two models differ, however, in structure, abstraction levels, and historical usage.
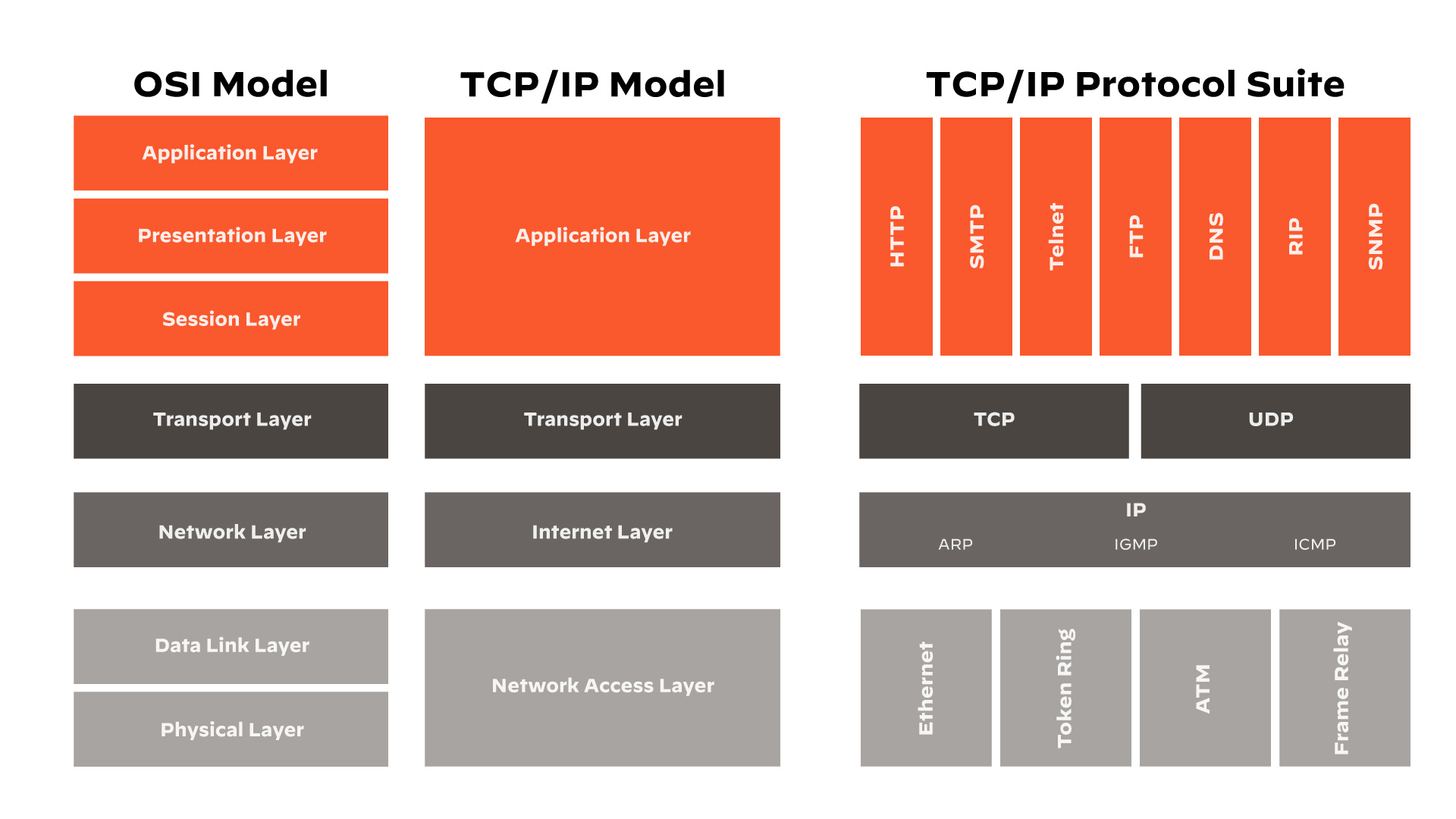
Structure and Abstraction Levels
The OSI model has seven layers, each layer providing a set of specific services and operating independently while interacting with the layers immediately above and below. The design, as intended, created a universal standard for all types of network communication.
The TCP/IP model is more focused on the realities of network communication and dismisses the modular separation of functionality, as seen in its four-layer structure.
- Network interface (equivalent to the physical and data link layers of the OSI model)
- Internet (equivalent to the network layer)
- Transport
- Application (combining the session, presentation and application layers of the OSI model)
Historical Usage
Despite its comprehensive design, the OSI model was never widely adopted for practical networking implementations. Its use has remained conceptual, serving as a tool to understand and describe network protocol interaction and operation.
In contrast, the TCP/IP Model was created and implemented as the foundation of the modern internet. TCP and IP, are the backbone protocols of the internet. The model was designed to solve practical networking problems and achieve effective wide-area communication, rather than to conform to a layered reference model.