Get Visibility
As the foundational element of our enterprise security platform, App-ID is always on. It uses multiple identification techniques to determine the exact identity of applications traversing your network, including those that try to evade detection by masquerading as legitimate traffic, by hopping ports or by using encryption. Combined with information from User-ID, you always know who is using what on your network.
Safely Enable Applications
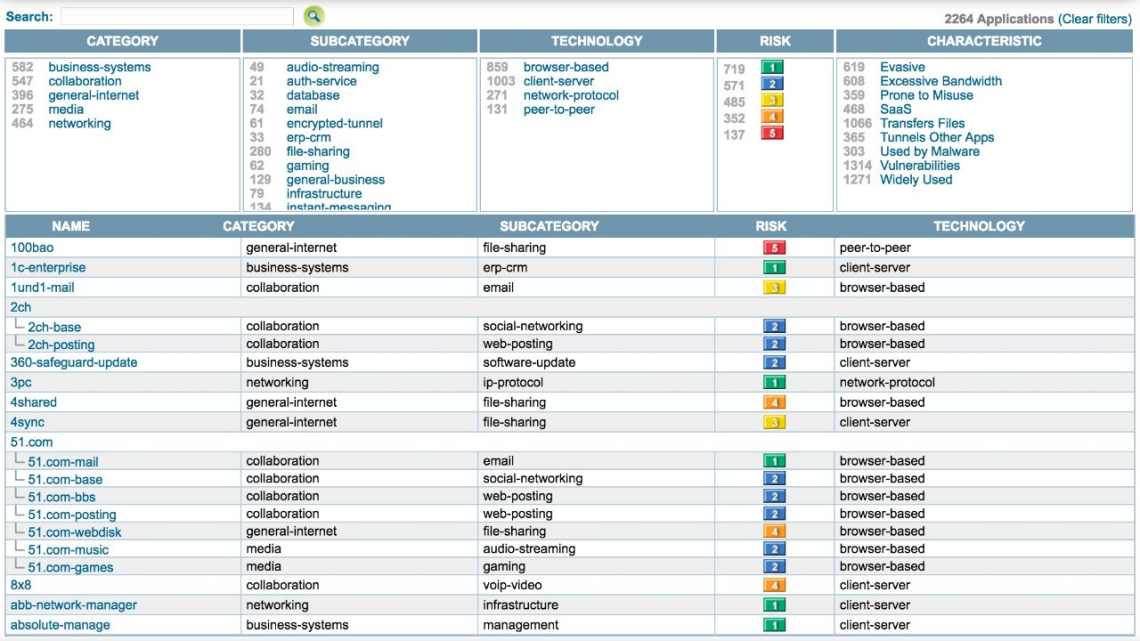
App-ID enables you to see the applications on your network and learn how they work, their behavioral characteristics, and their relative risk. Armed with this information, your security team can use positive security model rules to allow the applications or specific application functions that enable the business.
Reduce Attack Surface Area
Our next-generation firewalls support a positive enforcement model. You can allow sanctioned applications and application functions, and block or tightly control the remaining applications and unknown traffic. In addition, you can specify users and groups allowed to use the sanctioned applications. All of this allowed traffic is scanned for threats and sensitive data. This greatly reduces the surface area of cyber attacks across the organization.
App-ID enables you to see the applications on your network and learn how they work, their behavioral characteristics, and their relative risk. Applications and application functions are identified via multiple techniques, including application signatures, decryption (if needed), protocol decoding, and heuristics. This allows granular control, for example, allowing only sanctioned Office 365 accounts, or allowing Slack for instant messaging but blocking file transfer.
Broad and Deep Coverage, Yet Easy to Use
App-ID supports a comprehensive set of applications and application functions, organized by categories, technologies, risk and so on. This enables your organization to transition to a positive enforcement model and explicitly define which applications and application functions are allowed. In addition, you can create your own App-IDs for internal or custom applications.
"Unknown traffic," which is unrecognized by predefined and custom App-IDs, can be treated as its own category and explicitly managed with a variety of enforcement options based on your organization’s risk profile. This flexible handling of unknown traffic is unique to Palo Alto Networks.
Security Policies That Enable Your Business
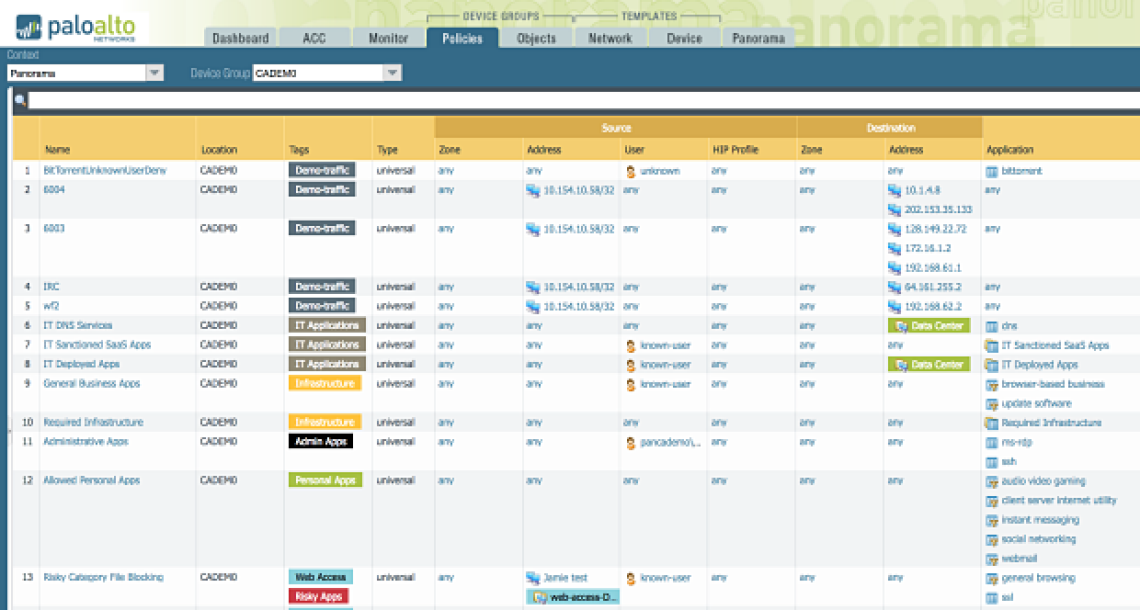
Applications and application functions are foundational elements for policy in our next-generation firewalls. Security policies can also specify dynamic application filters that apply enforcement to groups of applications that meet a combination of criteria, for example, by blocking file-sharing peer-to-peer applications or high-risk encrypted-tunnel applications. This automatically keeps your security rules up to date with new applications that match the criteria.
Extensive Visibility and Reporting
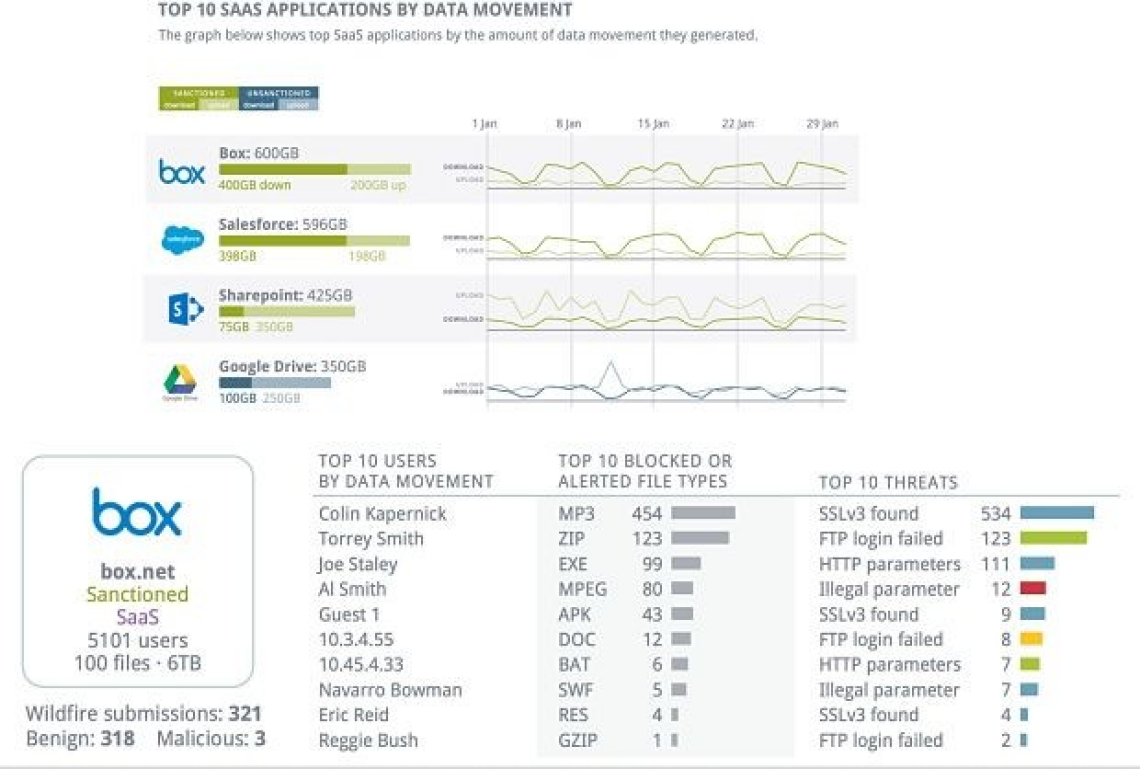
The Application Command Center (ACC) shows a highly interactive, graphical view of application, URL, threat and data traffic. The ability to drill down from high-level information to individual log entries makes it possible to get answers to important questions fast.
Predefined and custom reports help you share insights with others. One of the predefined reports is the SaaS Application Usage report, which shows the top sanctioned and unsanctioned SaaS applications running on your network. This helps you assess risks to the security of your network, such as the delivery of malware through SaaS applications adopted by your users.