After a successful migration to the cloud, a Fortune 500 global beverage manufacturer with 200+ sites in more than 100 countries required a solution to secure and protect the integrity of its supply chain while streamlining operations and lowering costs. The enterprise embarked on a journey to achieve Zero Trust, working with Palo Alto Networks, step by step, to remain competitive in the market by eliminating security gaps across its cloud environment, offices, and manufacturing facilities worldwide.
Greater complexity brings greater risk
After transitioning to the cloud, the organization:
- Suffered more than a dozen major ransomware incidents a year
- Needed to secure more than 25K employees globally
- Managed 6 different security vendors, each with its own policies, management planes, etc.
Turning Zero Trust principles into reality
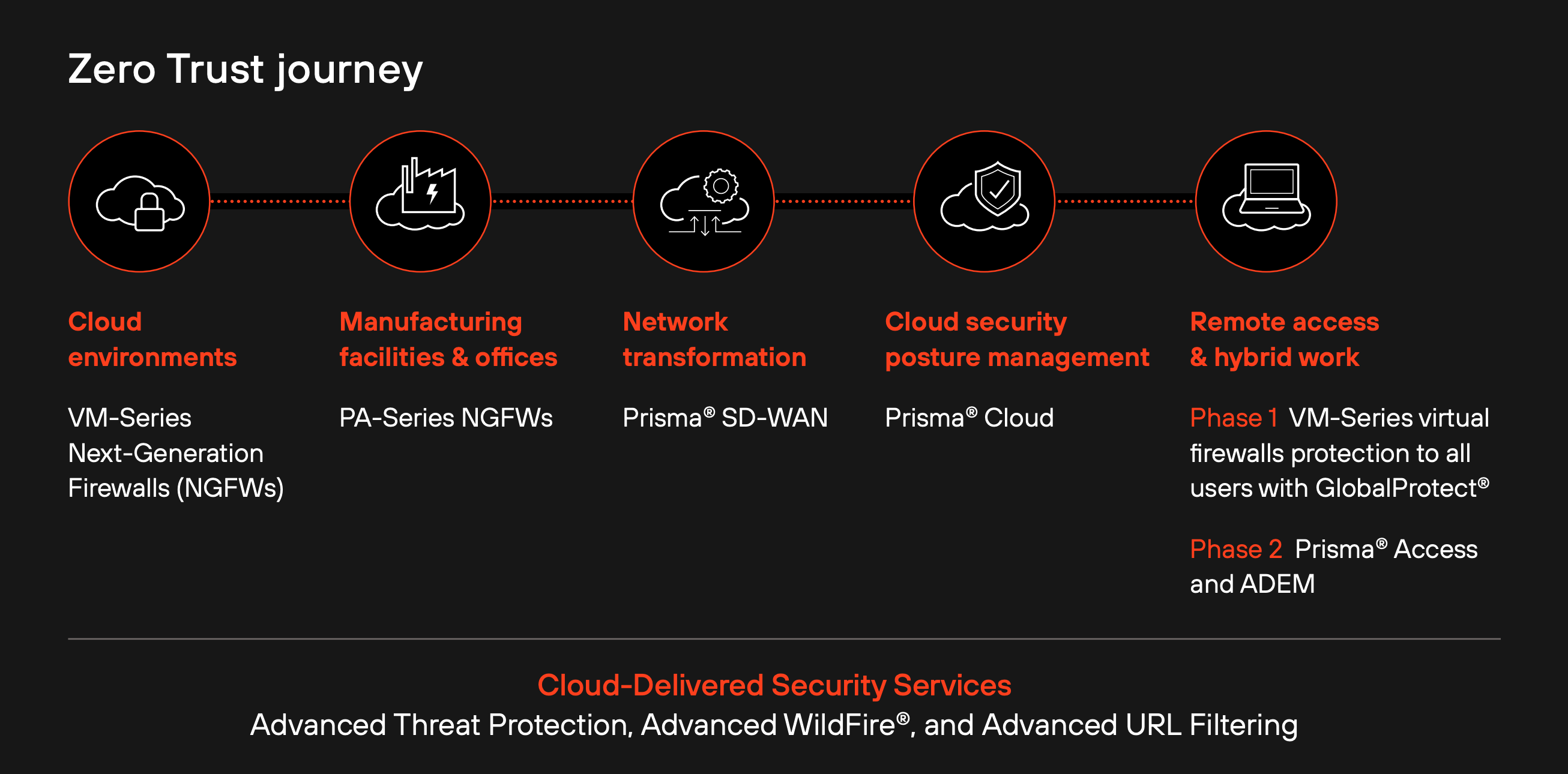
Beginning in 2017, the company partnered with Palo Alto Networks on network security solutions to modernize its enterprise. The organization aimed to adopt a Zero Trust framework, eliminating implicit trust in its environment and continuously validating every stage of its digital interactions.
Starting its journey with virtualized firewalls to protect cloud networks, the company quickly moved to secure and connect manufacturing sites with hardware firewalls and SD-WAN devices. The enterprise then further protected its cloud security posture and remote workers with SASE, regardless of whether employees were in Amsterdam, Adelaide, or Atlanta. Finally, GlobalProtect was deployed on 55K beverage machines with a bespoke solution to ensure secure transmission of critical inventory data in real time.
As a result of partnering with Palo Alto Networks, they've seen:
- A decrease to Zero ransomware incidents per year, down from >12
- A 75% reduction in compromised endpoint incidents for remote workers
- A 90% reduction in management overhead
- Millions of dollars in future savings by consolidating several vendors
"Security has to be at the core of everything we do. We are always a big threat target no matter what. We have to stay at the very forefront from a cyber perspective, leveraging the principles of Zero Trust. Thinking about security posture from end-user devices, through the network, to the application: You’re only as good as the weakest link in the chain.”"
– Head of Infrastructure
Operations, and Digital Workplace